- Joined
- May 13, 2017
- Messages
- 255
Hello everyone! In this post, I'll be demonstrating how to safeguard your website from DDoS attacks at no cost, and it's straightforward to set up.
Here are the things you'll need: your website is linked to Cloudflare CDN (https://support.cloudflare.com/hc/e...ing-a-Cloudflare-account-and-adding-a-website), and your website could be either WordPress-based or not.
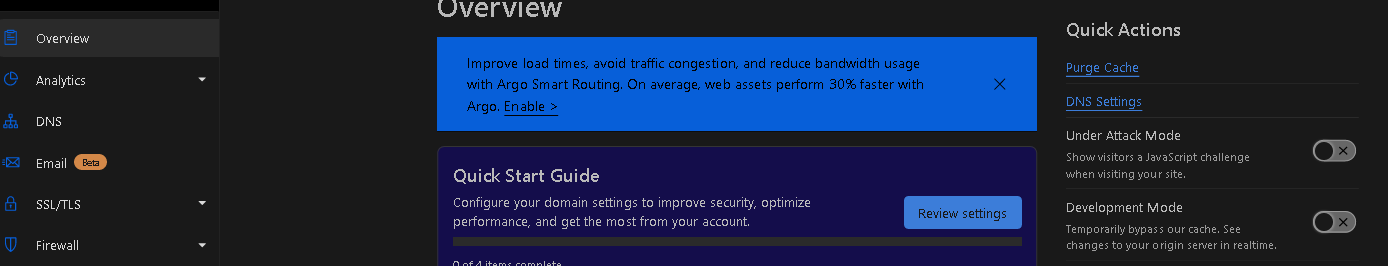
Once you navigate to your website's overview:
Let's begin by visiting the Firewall section, which can be found on the left-hand side of the menu, and then clicking on Firewall Rules.
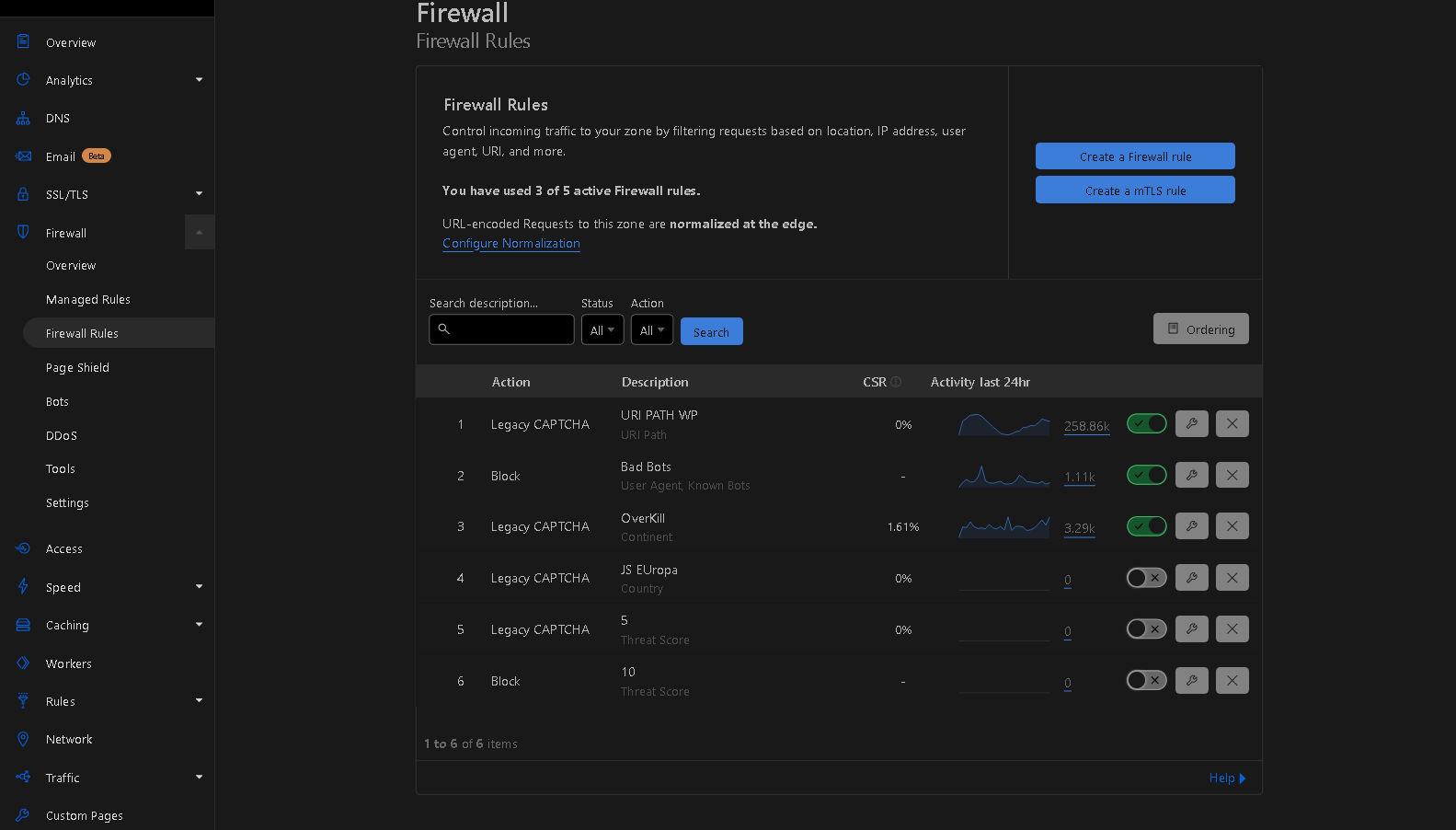
Here, you'll need to generate a few Firewall Rules by selecting "Create a Firewall rule." The initial rule we'll create is exclusively for WordPress-based websites and won't be beneficial if your website isn't using WordPress.
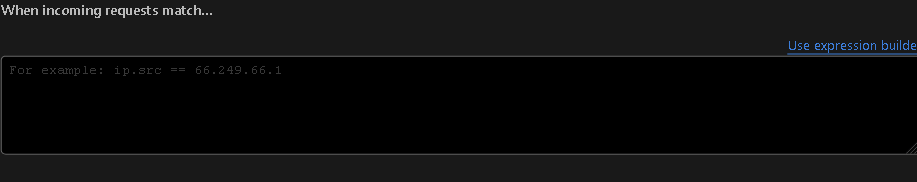
Upon visiting the "Create Firewall rule" section, you can name it anything you prefer since the name isn't critical. After that, select "Use expression builder" and paste the following code:
Then, select "Block" as the action.
These two rules will offer robust protection for your website. As for the third rule, it will safeguard you from spammers and provide some DDoS filtering.
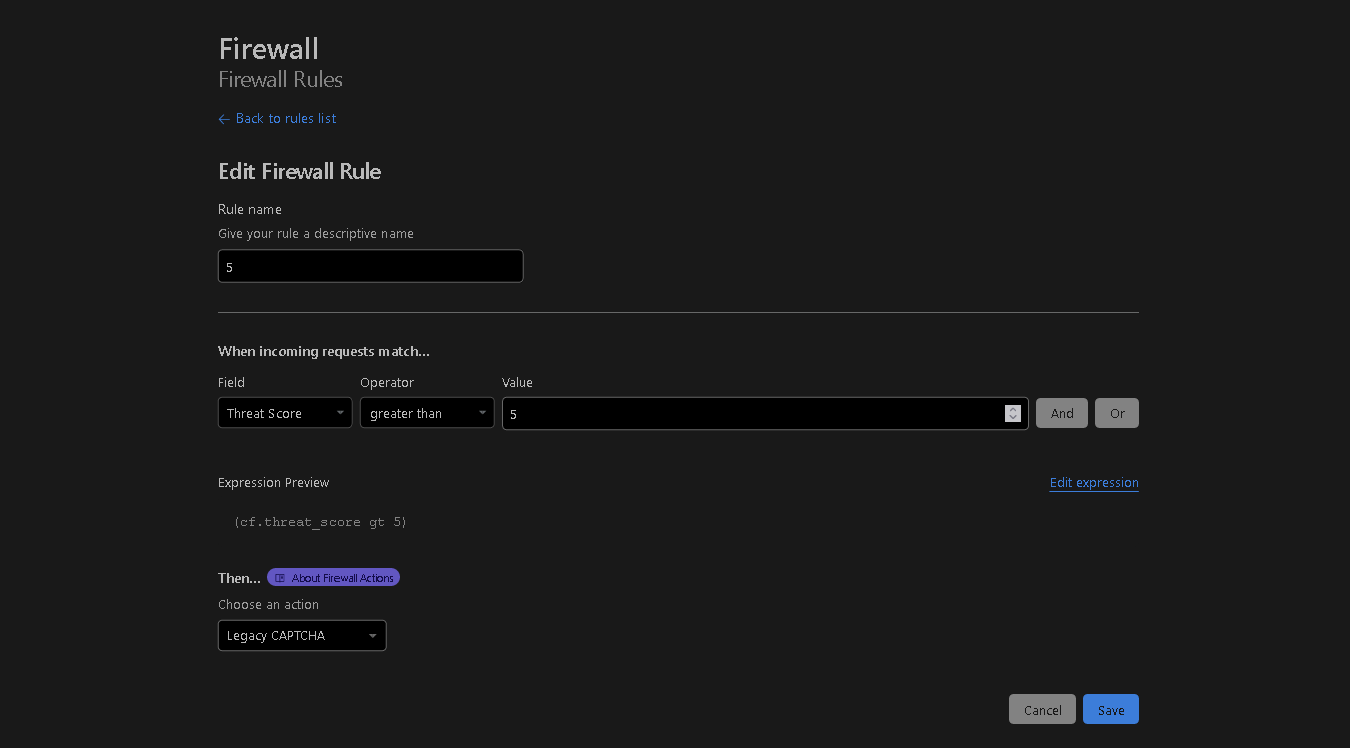
If an person's threat score surpasses 5, they should be given the Legacy Captcha. If none of the aforementioned methods have proven useful in combating the ongoing DDoS attack against your website, it's time to activate the "I'm under attack" mode.
On the right-hand side of the screen, you'll see "js," turn it on. Once the DDoS attack has subsided, don't forget to disable it and switch to "Hard."
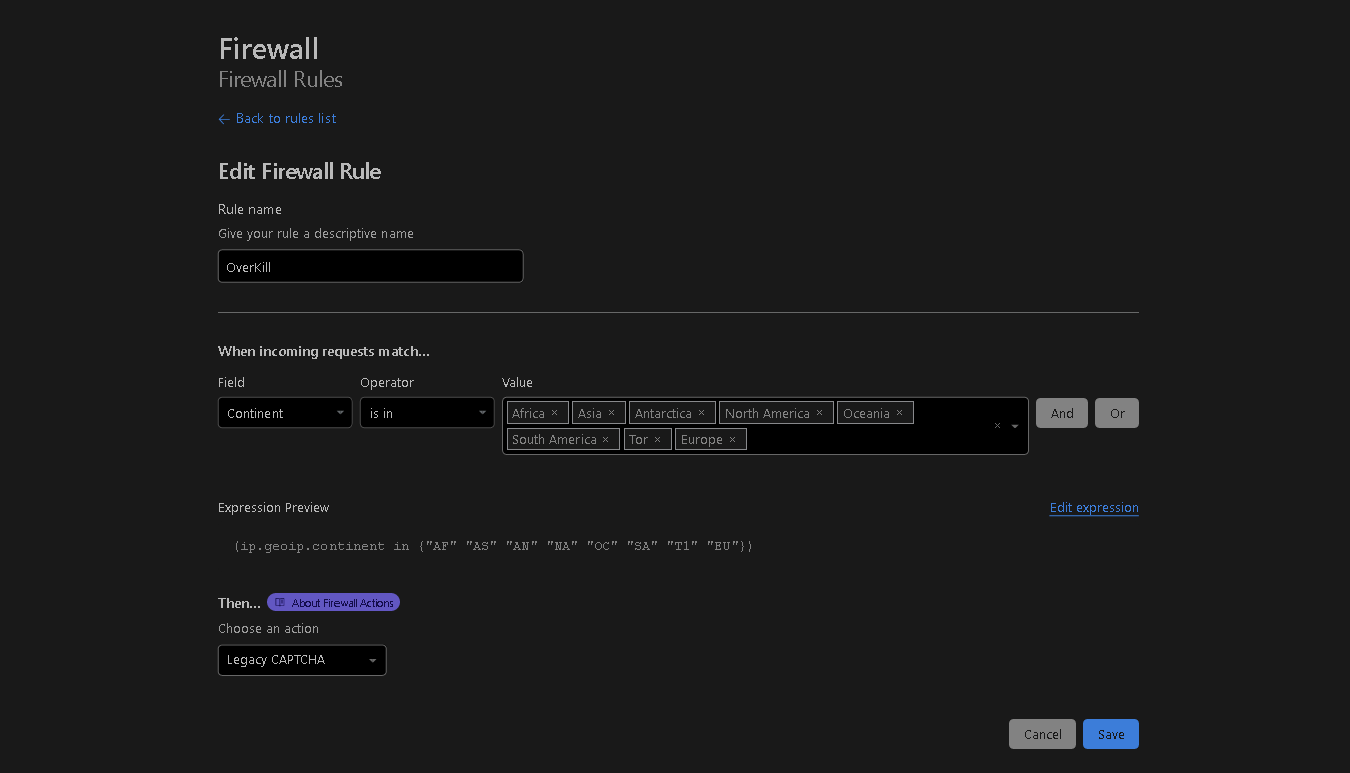
If none of the previous measures prove effective, it's time to implement the OverKill rule (a somewhat cringy name I came up with for this rule). If your website has a global audience and isn't specific to a single country, you should opt for a rule that imposes "Legacy CAPTCHA" on all continents.
If you feel that the previous measure is too taxing, you may consider implementing Legacy CAPTCHA on all continents, excluding the United States, for example, if the majority of your traffic originates from the US. Additionally, you could create another rule for placing all other North American countries under the Challenge action.
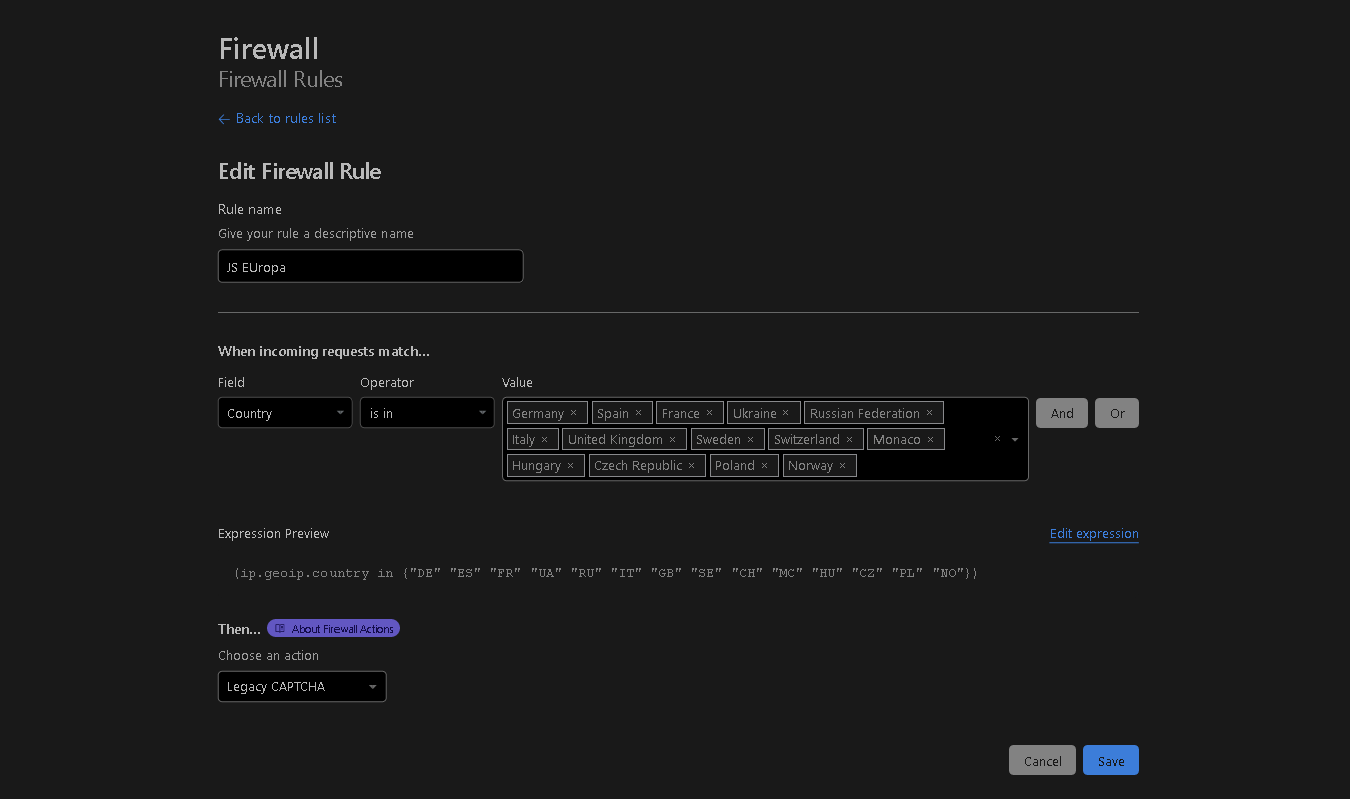
However, if your website caters to specific countries, this rule will be more advantageous for you. You can place all unimportant continents under Legacy CAPTCHA in one rule and include other countries on your continent under Legacy CAPTCHA as well, as demonstrated here:
What should be the next step?
Navigate to the "Bots" section.
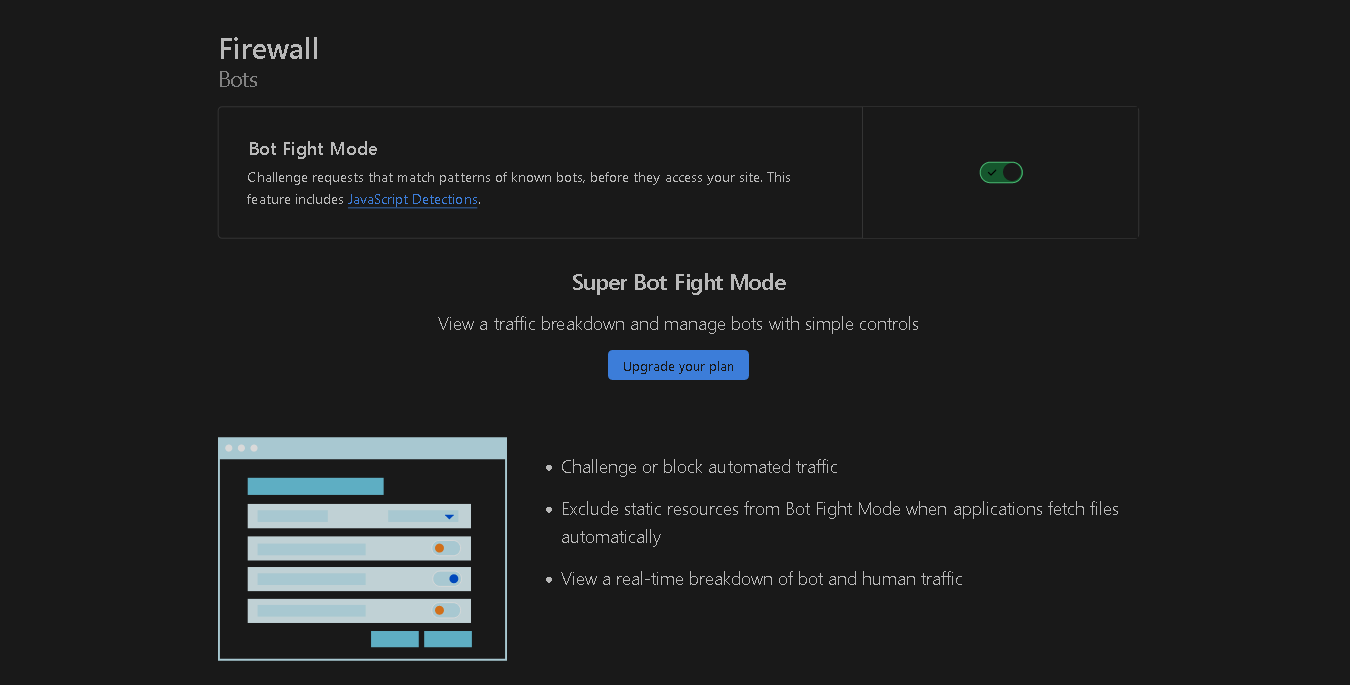
Navigate to the section labeled "Bots."
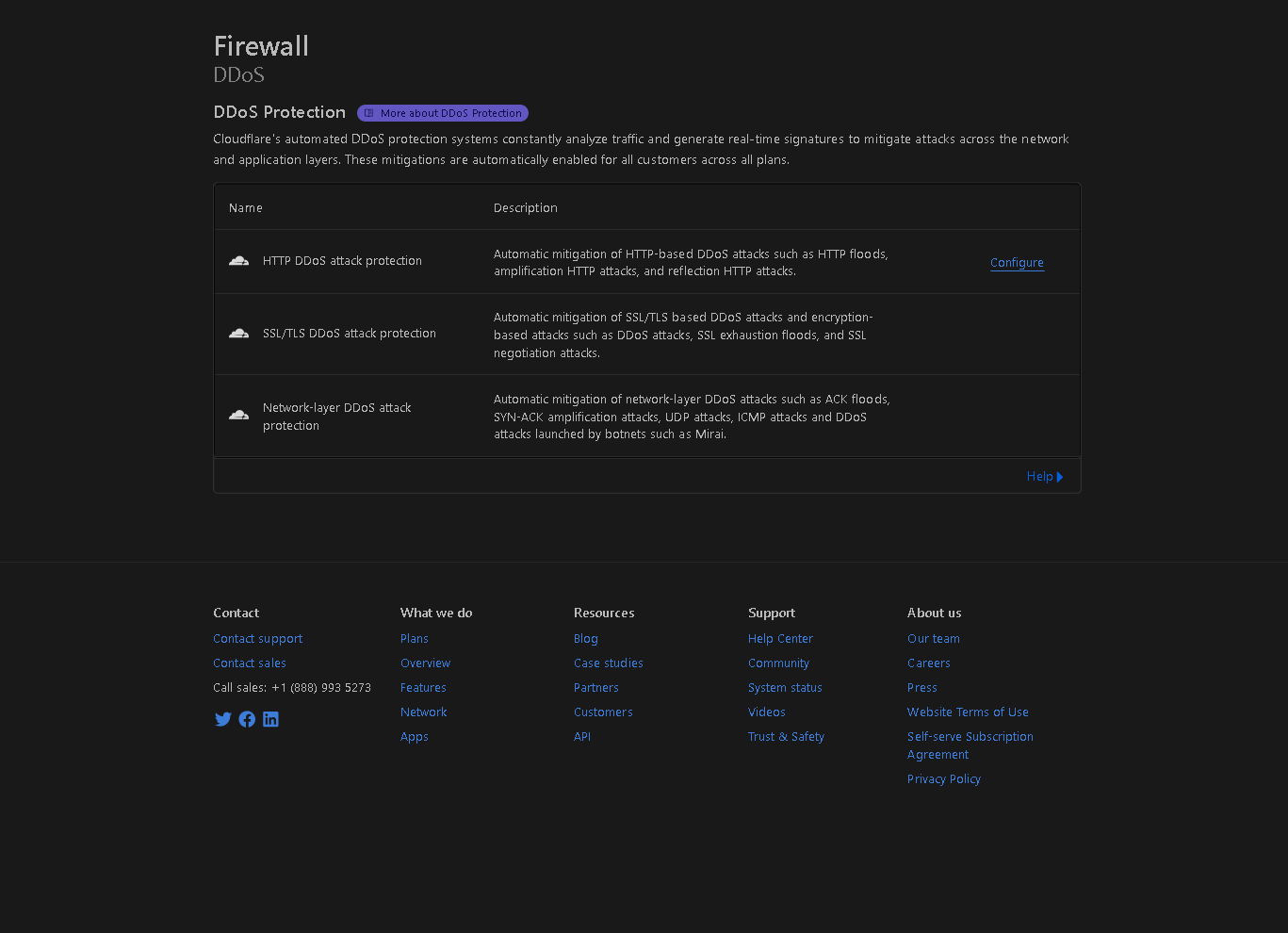
Activate the option. If you have followed all the aforementioned steps, you will have acquired some basic understanding of this topic, and you may also explore the "DDoS" tab in the menu.
That concludes the steps required to protect your website from DDoS attacks. If none of the aforementioned methods get positive results, it could indicate that your website isn't adequately optimized. Ensure that your website has a robust cache and optimization plugins. If many people request it, I will produce a guide on this topic in the future.
In conclusion, I hope you all have a wonderful day and excellent health. God bless you!
Here are the things you'll need: your website is linked to Cloudflare CDN (https://support.cloudflare.com/hc/e...ing-a-Cloudflare-account-and-adding-a-website), and your website could be either WordPress-based or not.
Once you navigate to your website's overview:

Let's begin by visiting the Firewall section, which can be found on the left-hand side of the menu, and then clicking on Firewall Rules.

Here, you'll need to generate a few Firewall Rules by selecting "Create a Firewall rule." The initial rule we'll create is exclusively for WordPress-based websites and won't be beneficial if your website isn't using WordPress.

Upon visiting the "Create Firewall rule" section, you can name it anything you prefer since the name isn't critical. After that, select "Use expression builder" and paste the following code:
(http.request.uri.path contains "/admin-ajax.php") or (http.request.uri.path contains "/wp-admin") or (http.request.uri.path contains "/wp-cron.php") or (http.request.uri.path contains "/wp-config.php") or (http.request.uri.path contains "/xmlrpc.php") or (http.request.uri.path contains "/wp-login.php") or (http.request.uri.path contains "/favicon.ico") or (http.request.uri.path contains "/wp-load.php") or (http.request.uri.path contains "/wp-includes") or (http.request.uri.path contains "/wp-json") or (http.request.uri.path contains "/?wp_service_worker=1")(http.user_agent contains "Yandex") or (http.user_agent contains "muckrack") or (http.user_agent contains "Qwantify") or (http.user_agent contains "Sogou") or (http.user_agent contains "BUbiNG") or (http.user_agent contains "knowledge") or (http.user_agent contains "CFNetwork") or (http.user_agent contains "Scrapy") or (http.user_agent contains "SemrushBot") or (http.user_agent contains "AhrefsBot") or (http.user_agent contains "Baiduspider") or (http.user_agent contains "python-requests") or (http.user_agent contains "crawl" and not cf.client.bot) or (http.user_agent contains "Crawl" and not cf.client.bot) or (http.user_agent contains "bot" and not http.user_agent contains "bingbot" and not http.user_agent contains "Google" and not http.user_agent contains "Twitter" and not cf.client.bot) or (http.user_agent contains "Bot" and not http.user_agent contains "Google" and not cf.client.bot) or (http.user_agent contains "Spider" and not cf.client.bot) or (http.user_agent contains "spider" and not cf.client.bot)Then, select "Block" as the action.
These two rules will offer robust protection for your website. As for the third rule, it will safeguard you from spammers and provide some DDoS filtering.

If an person's threat score surpasses 5, they should be given the Legacy Captcha. If none of the aforementioned methods have proven useful in combating the ongoing DDoS attack against your website, it's time to activate the "I'm under attack" mode.

On the right-hand side of the screen, you'll see "js," turn it on. Once the DDoS attack has subsided, don't forget to disable it and switch to "Hard."
If none of the previous measures prove effective, it's time to implement the OverKill rule (a somewhat cringy name I came up with for this rule). If your website has a global audience and isn't specific to a single country, you should opt for a rule that imposes "Legacy CAPTCHA" on all continents.

If you feel that the previous measure is too taxing, you may consider implementing Legacy CAPTCHA on all continents, excluding the United States, for example, if the majority of your traffic originates from the US. Additionally, you could create another rule for placing all other North American countries under the Challenge action.
However, if your website caters to specific countries, this rule will be more advantageous for you. You can place all unimportant continents under Legacy CAPTCHA in one rule and include other countries on your continent under Legacy CAPTCHA as well, as demonstrated here:

What should be the next step?

Navigate to the "Bots" section.

Navigate to the section labeled "Bots."

Activate the option. If you have followed all the aforementioned steps, you will have acquired some basic understanding of this topic, and you may also explore the "DDoS" tab in the menu.

That concludes the steps required to protect your website from DDoS attacks. If none of the aforementioned methods get positive results, it could indicate that your website isn't adequately optimized. Ensure that your website has a robust cache and optimization plugins. If many people request it, I will produce a guide on this topic in the future.
In conclusion, I hope you all have a wonderful day and excellent health. God bless you!